Ad Networks offer affiliate programs that allow affiliates to generate income. These affiliates are given an Affiliate ID that stores a cookie in a user’s browser for a specified period of time. If the user makes a sale/conversion before the cookie expires, the affiliate receives a commission for that sale/conversion.
What makes this cookie stuffing approach unique is that it does not technically distribute any malicious content. If a user engaged with the page containing the iFrame on the compromised website, they simply transferred a network’s affiliate cookie to the user’s browser.
What is an iFrame and How it’s Misused?
An iFrame is an HTML code that allows one web page to display another one. It is often used by advertisers to place ads, banners, or other creatives onto a publishers’ website.
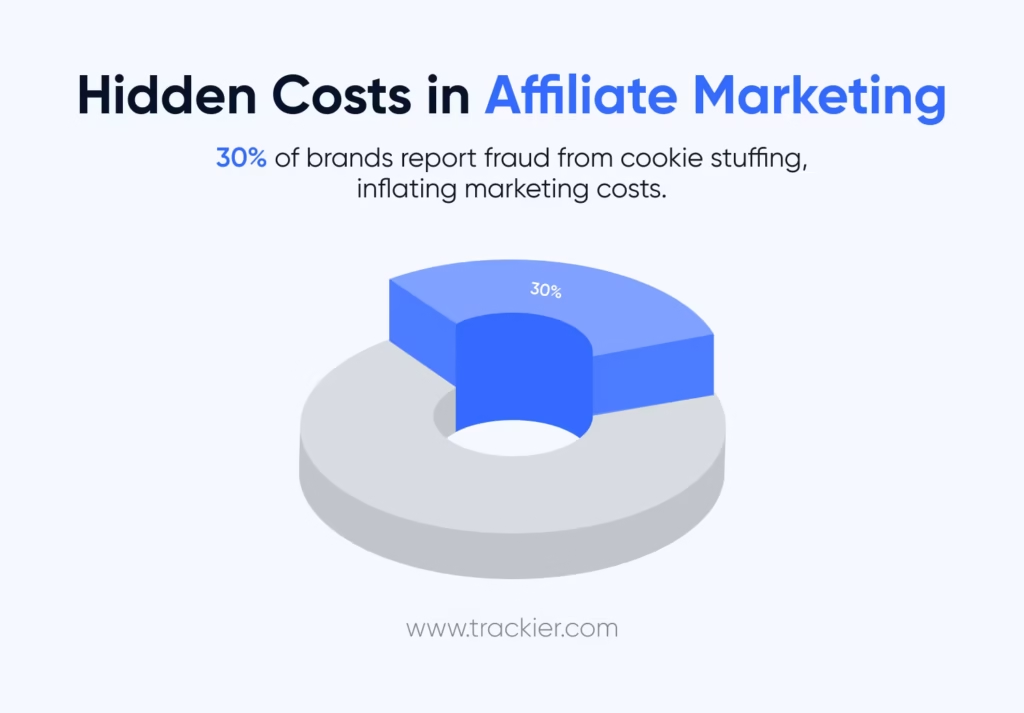
As per the reports, up to 62% of all affiliate fraud is attributed to cookie stuffing tactics. In some cases, however, affiliates have misused this feature by inserting a hidden iFrame that contains an affiliate tracking url.
Here is an example of a publisher using an iFrame pixel to stuff cookies on the user browser and generate fraudulent conversions:

When users visit a web page with a hidden iFrame like this, their browser loads all the content whether the user can see it or not. This includes affiliate cookies, which are then stored in the browser.
Some fraudsters will inject even 20 or more hidden iFrames on a single page to multiply their chances of stealing commissions. They will never see the page, so it doesn’t matter what the site speed is, and there’s nothing worse than a poor user experience.
If the user makes a conversion before the injected iFrame cookie expires, network will receive a commission for the purchase.
By compromising more websites and distributing their injected Affiliate iFrames exposure is maximized as is the number of commissions generated for these black hat marketers clearly showing that unprotected websites are a resource valuable for bad actors.
To mitigate the risk of serving unwanted affiliate cookies or reducing site performance, website owners can closely monitor changes to their website files by using an integrity monitoring service. This service will make it easy to spot any suspicious or compromised activity.
Other Forms of Cookie Stuffing
iFrame stuffing is certainly the most common cookie stuffing method but there are other techniques that fraudsters use.
- Pop-ups and Pop-unders: Small pop-up windows can pop-up on a site. They run in the background and without any user interaction drop cookies on the computer.
- JavaScript Cookie Injection: Using JavaScript snippets are used to automatically set cookies when the page loads.
- Image Pixel Stuffing: These functions similar to iFrames but actually rely on the use of invisible 1×1 pixel images that carry affiliate tracking links.
- Toolbar/Extension Stuffing: Browser extensions can install tracking cookies when browsing the internet and do so silently in the background.
In all of the above cookie stuffing examples, both are ultimately aimed at the same end-user result. They allow the fraudster to earn a commission on a conversion without ever doing anything.
Why is Cookie Stuffing Dangerous?
Cookie stuffing isn’t just harmful to advertisers, it harms the entire performance marketing ecosystem.
- For Advertisers: They are effectively paying commissions for conversions they would have received anyway. This inflates their marketing costs, and makes it impossible to calculate an ROI.
- For Legitimate Affiliates: Legitimate affiliates are working hard for no reward because, by the time they send the user to the advertiser’s site, a cookie has already been placed in the user’s browser overhead by a fraudulent affiliate. This destroys any credibility the affiliates are trying to build with their advertisers’ programs.
- For Users: Although cookie stuffing doesn’t have a direct impact on them, it negatively affects their browsing experience, increases the time for websites to load, and can actually drain resources or processes on their device.
- For Networks: There is a lack of trust between advertisers and affiliates, and it can damage long-term relationships over a lack of trust.
In fact, cookie stuffing has given rise to several lawsuits in the affiliate industry, as fraudsters have resulted in large brands suing them for millions in damages.
How Can Businesses Protect Themselves?
Cookie stuffing may be difficult to detect, but businesses can take some actions to mitigate cookie stuffing and its effects:
- File Integrity Monitoring: Monitor website code so you can detect unauthorized changes like hidden iFrames.
- Fraud Detection Systems: Use advanced tracking platform and build your tools using Trackier to identify sudden spikes in traffic, duplicate clicks, and suspicious changes in conversions.
- Analyze Conversions: Assess your conversion tracking data based on device ID, IP address, and time-stamp to identify any strange, out of the ordinary transactions.
- Consider Shorter Cookie Windows: By narrowing the cookie attribution windows that many affiliate businesses or networks have, your business may exposure to fraud risks.
What Trackier is Doing to Stop This Fraud?
At Trackier, we are committed to combatting affiliate fraud. That’s why we have implemented a dedicated fraud shield protection against cookie stuffing.
- Trackier monitors any and all traffic 24/7, which can track unwanted suspicious activity coming from iFrames or image pixels.
- Any click that is flagged from a hidden stuffing technique is blocked automatically.
- This allows advertisers to not waste money advertising on fraudulent conversions, while also providing genuine affiliates with the proper reward.
This only helps business also to avoid unwanted traffic, so that they our partners maintain a healthy conversion rate. Make your campaigns big with Trackier fraud prevention, you don’t have to worry about hidden the hidden threat of cookie stuffing.
Conclusion
Cookie stuffing may not seem harmful at first glance, as it doesn’t cause harm to the user. However, it is one of the most dishonest and destructive types of affiliate fraud in the market. It not only steals budgets meant for advertisers, but it also harms honest affiliates and reduce trust in performance marketing.
As the industry grows, so does fraudulent activity, and so does ingenuity. That is why it is important for businesses to look Trackier that provides an anti-fraud functionality as part of its tracking, not just as a tracking feature to make money. Be safe, be profitable, and let the affiliate who deserves it, to get its corresponding reward.
FAQs
1. How does Trackier stop cookie stuffing fraud?
Trackier’s fraud protection blocks suspicious clicks associated with iFrame or image pixel stuffing. Our servers monitor traffic 24/7, filtering for abnormal activity automatically. We aim to ensure our advertisers don’t spend their budgets on fake conversions, while rewarding legitimate affiliates so they are not penalized for promoting their business.
2. What can advertisers do to protect themselves from cookie stuffing?
Advertisers need to use a fraud detection tool, monitor the integrity of websites, qualify their affiliates, and audit conversions. Limiting attribution windows, and looking for anomalies in the traffic the affiliates drive can also help. Using a more comprehensive tracking platform like Trackier offers further protection, and helps to ensure fraudsters can’t take advantage of the affiliate’s program for their own benefit.
3. How can businesses detect cookie stuffing?
Through traffic analysis, conversion audits, and then integrity monitoring. Unexpected spikes in clicks along with abnormally high combinations or unknown referral sources generally signal fraud. Utilizing Trackier makes it easy to spot abnormal behavior, block fraudulent traffic, and similarly, prevent businesses from paying affiliates for fraudulent conversions.
4. What legal consequences can cookie stuffing have?
Cookie stuffing is considered fraud and lawsuits have arisen from the affiliate marketing industry because of it. Brands have sued fraudulent affiliates for damages sometimes millions of dollars. Additionally to downright fraud and potentially substantial financial losses, the participant opens themselves up to risk with respect to lose of partnership, reputation, and a permanent ban from affiliate programs or networks which comply with strict compliance standards.
5. What are some of the common techniques of cookie stuffing?
Common techniques are iFrame stuffing, image pixel stuffing, pop-ups or pop-unders, JavaScript cookie injection, and browser toolbars or extensions. Each method installs affiliate cookies without the user’s knowledge. Cookie stuffers may use several of these methods at once, installing dozens of cookies simultaneously, to try to increase their chances of payment on an unsolicited basis from advertisers or adjacent networks.